Open and manage cases in Kibana
Serverless Stack
Open a new case to keep track of issues and share their details with colleagues. You can create and manage cases using the cases UI.
Requirements
To access and send cases to external systems, you need the appropriate subscription or feature tier, and your role must have the required Kibana feature privileges. Refer to Configure access to cases in Kibana for more information.
To open a case:
Go to Management > Stack Management > Cases, then click Create case.
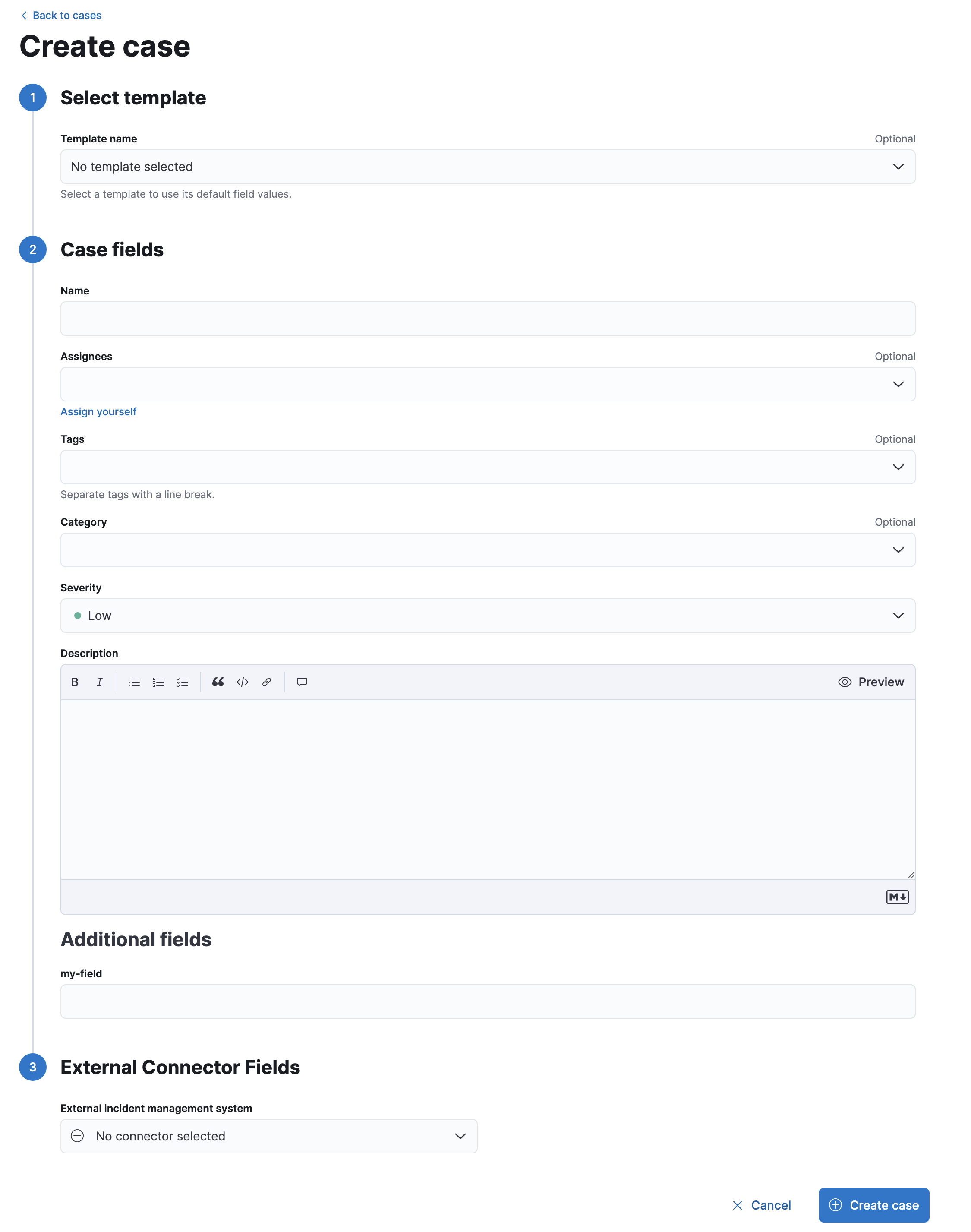
If you defined templates, you can optionally select one to use its default field values.
Give the case a name, severity, and description.
TipIn the
Descriptionarea, you can use Markdown syntax to create formatted text.Optionally, add a category, assignees, and tags. You can add users only if they meet the necessary prerequisites.
If you defined any custom fields, they appear in the Additional fields section.
(Optional) Under External Connector Fields, you can select a connector to send cases to an external system. If you’ve created any connectors previously, they will be listed here. If there are no connectors listed, you can create one. For more information, refer to External incident management systems.
Note StackWhen specifying Additional fields for an IBM Resilient connector, fields that are set when an incident is created or changed (for example, an incident is closed) won't display as an option.
After you’ve completed all of the required fields, click Create case.
Stack Serverless Alternatively, you can configure your rules to automatically create cases by using case actions. By default, the rule adds all of the alerts within a specified time window to a single case. You can optionally choose a field to group the alerts and create separate cases for each group. You can also choose whether you want the rule to reopen cases or open new ones when the time window elapses.
You can configure email notifications that occur when users are assigned to cases.
For Kibana on Elastic Cloud:
Add the email domains to the notifications domain allowlist.
You do not need to take any more steps to configure an email connector or update Kibana user settings, since the preconfigured Elastic-Cloud-SMTP connector is used by default.
For self-managed Kibana:
Create a preconfigured email connector.
NoteAt this time, email notifications support only preconfigured connectors, which are defined in the
kibana.ymlfile. For examples, refer to Email connectors and Configure email accounts for well-known services.Set the
notifications.connectors.default.emailKibana setting in kibana.yml to the name of your email connector.notifications.connectors.default.email: ‘mail-dev’ xpack.actions.preconfigured: mail-dev: name: preconfigured-email-notification-maildev actionTypeId: .email config: service: other from: from address host: host name port: port number secure: true/false hasAuth: true/falseIf you want the email notifications to contain links back to the case, you must configure the server.publicBaseUrl setting.
When you subsequently add assignees to cases, they receive an email.
You can also optionally add visualizations. For example, you can portray event and alert data through charts and graphs.
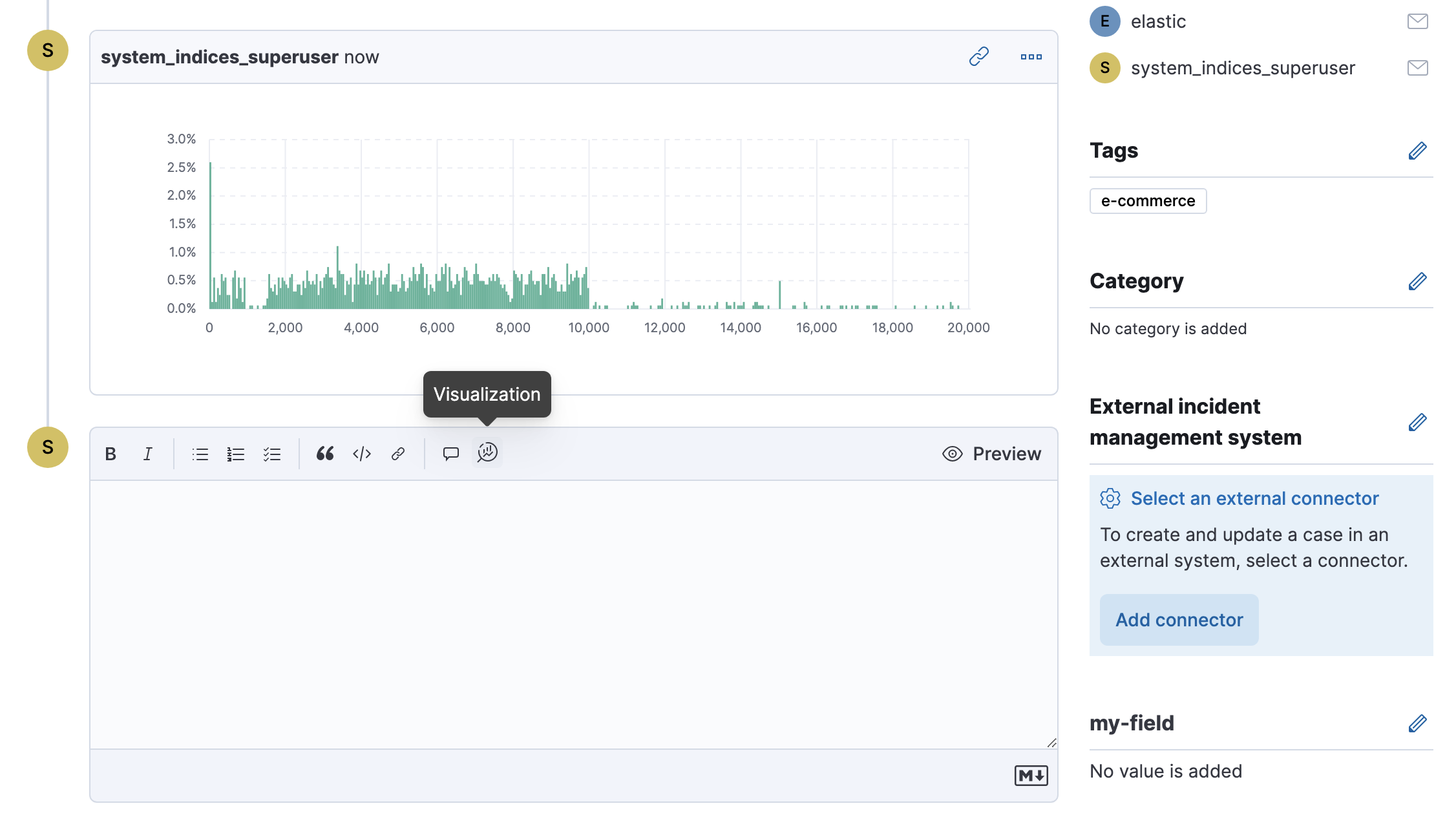
To add a visualization to a comment within your case:
Click the Visualization button. The Add visualization dialog appears.
Select an existing visualization from your Visualize Library or create a new visualization.
ImportantSet an absolute time range for your visualization. This ensures your visualization doesn’t change over time after you save it to your case and provides important context for viewers.
After you’ve finished creating your visualization, click Save and return to go back to your case.
Click Preview to see how the visualization will appear in the case comment.
Click Add Comment to add the visualization to your case.
Alternatively, while viewing a dashboard you can open a panel’s menu then click More > Add to existing case or More > Add to new case.
After a visualization has been added to a case, you can modify or interact with it by clicking the Open Visualization option in the case’s comment menu.
In Management > Stack Management > Cases, you can search cases and filter them by attributes such as assignees, categories, severity, status, and tags. You can also select multiple cases and use bulk actions to delete cases or change their attributes.
Stack To find cases that were created during a specific time range, use the date time picker above the Cases table. The default time selection is the last 30 days. Clicking Show all cases displays every Stack Management case in your space. The action also adjusts the starting time range to the date of when the first case was created.
To view a case, click on its name. You can then:
- Add and edit the case's description, comments, assignees, tags, status, severity, and category.
- Add a connector (if you did not select one while creating the case).
- Send updates to external systems (if external connections are configured).
- Refresh the case to retrieve the latest updates.
Provide additional context and resources by adding the following to the case:
From the Attachments tab, you can search for specific observable values, alert IDs, and file names.
Escalate alerts and track them in a single place by attaching them to cases. To examine the alerts, click the Alerts tab in the case. In the table, alerts are organized from oldest to newest. To view alert details, click the View details button.
You can find the Alerts tab in the following places:
- Stack : Go to the case's details page, then select the Attachments tab.
- Stack : Go to the case's details page.
Each case can have a maximum of 1,000 alerts.
Refer to View and manage alerts in Elastic Observability > Add alerts to cases to learn how to add alerts to cases.
After you create a case, you can upload and manage files on the Files tab. To find the tab:
- Stack : Go to the case's details page, then select the Attachments tab.
- Stack : Go to the case's details page.
To download or delete the file or copy the file hash to your clipboard, open the action menu . The available hash functions are MD5, SHA-1, and SHA-256.
When you upload a file, a comment is added to the case activity log. To view an image, click its name in the activity or file list.
Uploaded files are also accessible from the Files management page, which you can find using the navigation menu or entering Files into the global search field.
When you export cases as saved objects, the attached case files are not exported.
When you export cases as saved objects, the attached case files are not exported.
Uploaded files are also accessible from the Files management page, which you can find using the navigation menu or entering Files into the global search field.
An observable is a piece of information about an investigation, for example, a suspicious URL or a file hash. Use observables to identify correlated events and better understand the severity and scope of a case.
View and manage observables from the Observables tab. You can find the tab in the following places:
- Stack : Go to the case's details page, then select the Attachments tab.
- Stack : Go to the case's details page.
Each case can have a maximum of 50 observables.
To create an observable:
Click Add observable from the Observables tab.
Provide the necessary details:
- Type: Select a type for the observable. You can choose a preset type or a custom one.
- Value: Enter a value for the observable. The value must align with the type you select.
- Description (Optional): Provide additional information about the observable.
Click Add observable.
After adding an observable to a case, you can remove or edit it by using the Actions menu (…).
Go to the Similar cases tab to access other cases with the same observables.
The Cases page has a search bar for quickly finding cases and case data. You can search for case titles, descriptions, and IDs using keywords and text. Note the following rules for search:
- Keywords: Searches for keywords (like case and alert IDs) must be exact.
- Text: Text searches (such as case titles and descriptions) are case-insensitive.
- Syntax: No special syntax is required when entering your search criteria.
Stack You can also search for alert and event IDs, observable values, case comments, and custom fields (text type only). For example, you can search for a specific IP address that's been specified as an observable, a colleague's comment, or the ID of an alert that's attached to the case.