Manually configure security in a self-managed cluster
Self Managed
Security needs vary depending on whether you’re developing locally on your laptop or securing all communications in a production environment. Regardless of where you’re deploying the Elastic Stack ("ELK"), running a secure cluster is incredibly important to protect your data. That’s why security is enabled and configured by default in Elasticsearch 8.0 and later.
If you want to enable security on an existing, unsecured cluster, use your own Certificate Authority (CA), or would rather manually configure security, the following scenarios provide steps for configuring TLS on the transport layer, plus securing HTTPS traffic if you want it.
If you configure security manually before starting your Elasticsearch nodes, the auto-configuration process will respect your security configuration. You can adjust your TLS configuration at any time, such as updating node certificates.
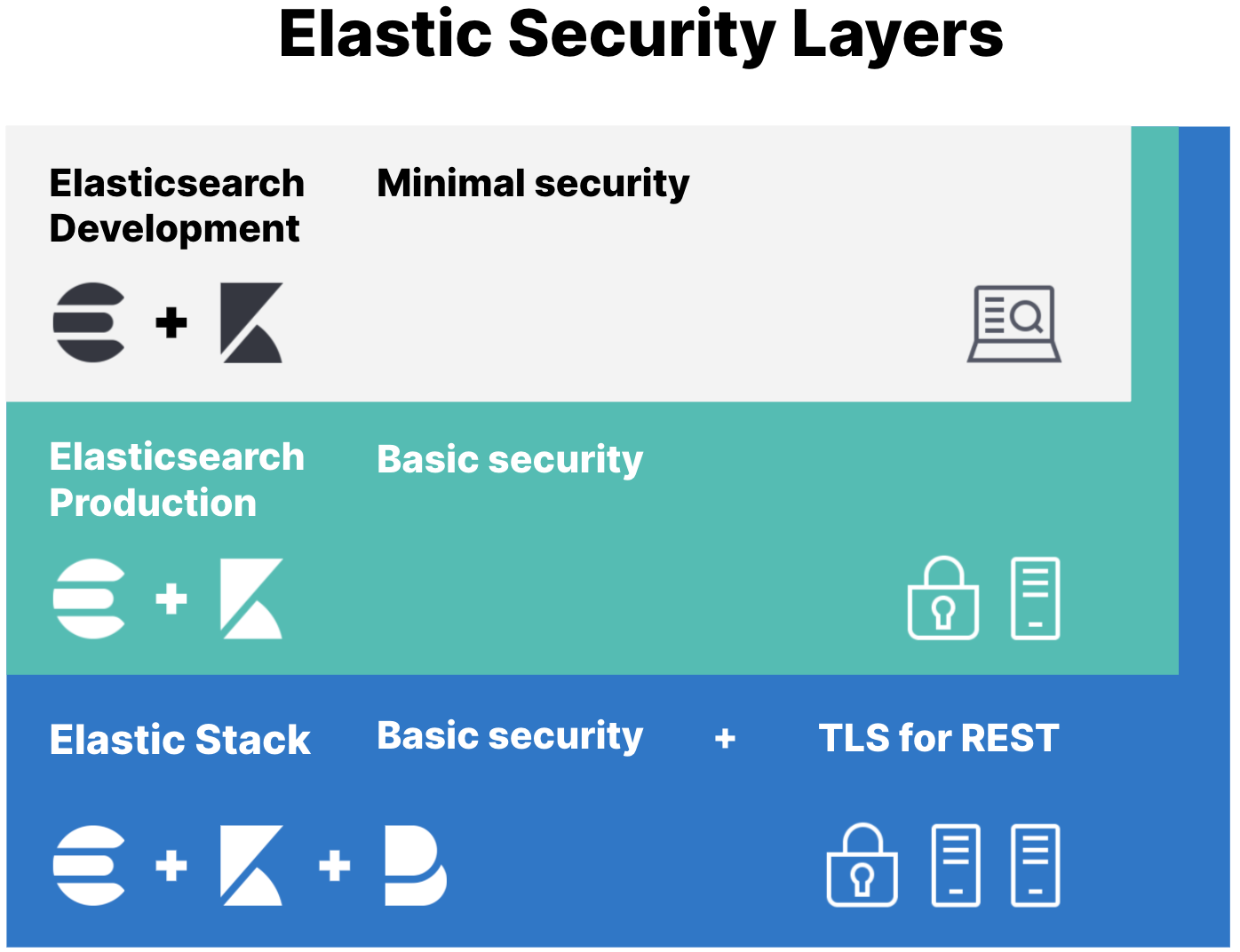
If you’ve been working with Elasticsearch and want to enable security on your existing, unsecured cluster, start here. You’ll set passwords for the built-in users to prevent unauthorized access to your local cluster, and also configure password authentication for Kibana.
The minimal security scenario is not sufficient for production mode clusters. If your cluster has multiple nodes, you must enable minimal security and then configure Transport Layer Security (TLS) between nodes.
This scenario configures TLS for communication between nodes. This security layer requires that nodes verify security certificates, which prevents unauthorized nodes from joining your Elasticsearch cluster.
Your external HTTP traffic between Elasticsearch and Kibana won’t be encrypted, but internode communication will be secured.
This scenario builds on the one for basic security and secures all HTTP traffic with TLS. In addition to configuring TLS on the transport interface of your Elasticsearch cluster, you configure TLS on the HTTP interface for both Elasticsearch and Kibana.
If you need mutual (bidirectional) TLS on the HTTP layer, then you’ll need to configure mutual authenticated encryption.
You then configure Kibana and Beats to communicate with Elasticsearch using TLS so that all communications are encrypted. This level of security is strong, and ensures that any communications in and out of your cluster are secure.
Set up basic security plus HTTPS traffic
TLS certificates apply security controls to network communications. They encrypt data in transit, verify the identity of connecting parties, and help prevent man-in-the-middle attacks.
On self-managed installations, you manage certificates for both HTTP and transport layers.
Control which systems can access your Elastic deployment through traffic filtering and network controls:
- IP traffic filtering: Restrict access based on IP addresses or CIDR ranges.
This section covered security principles and options at the environment level. You can take further measures individually for each deployment or cluster that you're running on your installation. Refer to Secure your cluster or deployment.