Elasticsearch API keys
Elastic Stack
Several types of Elasticsearch API keys exist:
- Personal/User API key: allows external services to access the Elastic Stack on behalf of a user.
- Cross-cluster API key: allows other clusters to connect to this cluster.
- Managed API key: created and managed by Kibana to run background tasks.
To manage API keys in Kibana, go to the API Keys management page using the navigation menu or the global search field.
- To use API keys in Kibana, you must have the
manage_security,manage_api_key, or themanage_own_api_keycluster privileges. - To delete API keys, you must have the
manage_api_keyormanage_own_api_keyprivileges. - To create or update a user API key, you must have the
manage_api_keyor themanage_own_api_keyprivilege. - To create or update a cross-cluster API key, you must have the
manage_securityprivilege and an Enterprise license. - To have a read-only view on the API keys, you must have access to the page and the
read_securitycluster privilege.
To manage roles, go to the Roles management page using the navigation menu or the global search field, or use the role APIs.
To create an API key, go to the API Keys management page using the navigation menu or the global search field, and select Create API key.
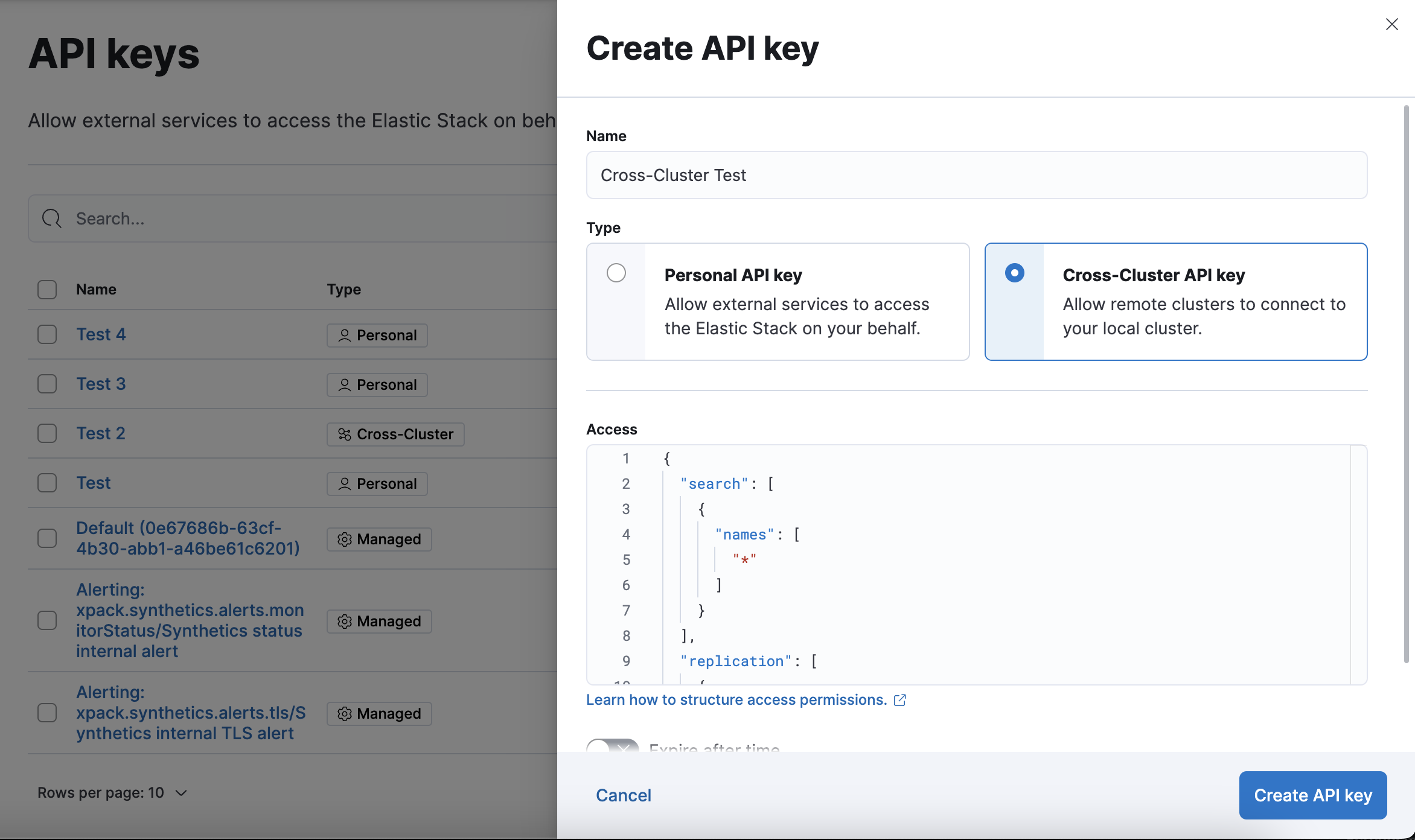
Refer to the Create API key documentation to learn more about creating user API keys.
Refer to the Create cross-cluster API key documentation to learn more about creating cross-cluster API keys.
To update an API key, go to the API Keys management page using the navigation menu or the global search field, and then click on the name of the key. You cannot update the name or the type of API key.
Refer to the Update API key documentation to learn more about updating user API keys.
Refer to the Update cross-cluster API key documentation to learn more about updating cross-cluster API keys.
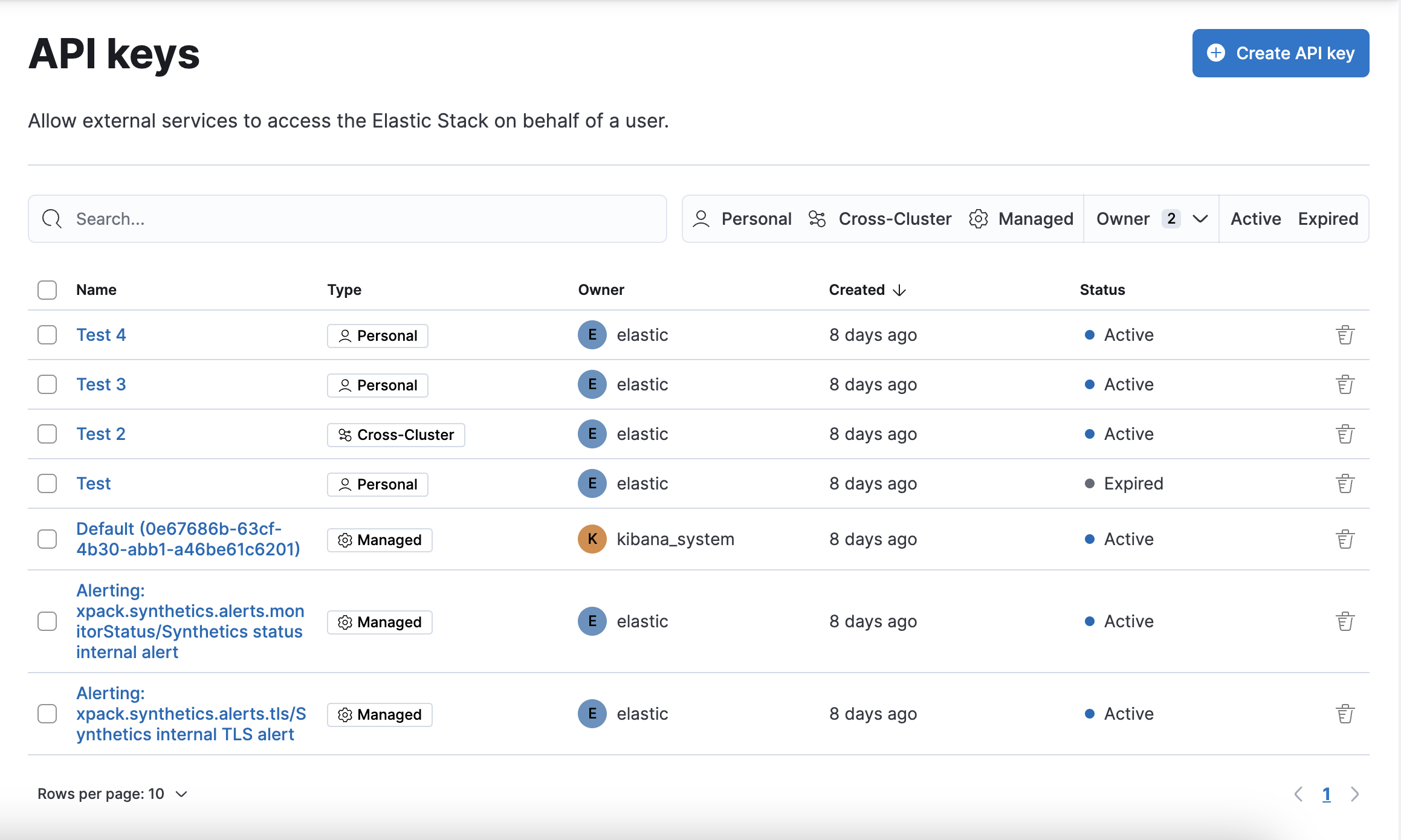
The API Keys feature in Kibana lists your API keys, including the name, date created, and status. If an API key expires, its status changes from Active to Expired.
If you have manage_security or manage_api_key permissions, you can view the API keys of all users, and see which API key was created by which user in which realm. If you have only the manage_own_api_key permission, you see only a list of your own keys.
You can delete API keys individually or in bulk, but you need the manage_api_keys or manage_own_api_key privileges.