Configure security in a self-managed cluster
Self Managed
This page describes important aspects to consider and common end-to-end scenarios for securing your self-managed Elastic Stack. For a more granular view of the available security options for your clusters and nodes, refer to Secure your cluster or deployment.
Security needs vary depending on whether you’re developing locally on your laptop or securing all communications in a production environment. Regardless of where you’re deploying the Elastic Stack ("ELK"), running a secure cluster is incredibly important to protect your data. That’s why security is enabled and configured by default since Elasticsearch 8.0.
Never run an Elasticsearch cluster without security enabled. This principle cannot be overstated. Running Elasticsearch without security leaves your cluster exposed to anyone who can send network traffic to Elasticsearch, permitting these individuals to download, modify, or delete any data in your cluster. Start the Elastic Stack with security enabled or manually configure security to prevent unauthorized access to your clusters and ensure that internode communication is secure.
Never try to run Elasticsearch as the root user, which would invalidate any defense strategy and permit a malicious user to do anything on your server. You must create a dedicated, unprivileged user to run Elasticsearch. By default, the rpm, deb, docker, and Windows packages of Elasticsearch contain an elasticsearch user with this scope.
Even with security enabled, never expose Elasticsearch to public internet traffic. Using an application to sanitize requests to Elasticsearch still poses risks, such as a malicious user writing _search requests that could overwhelm an Elasticsearch cluster and bring it down. Keep Elasticsearch as isolated as possible, preferably behind a firewall and a VPN. Any internet-facing applications should run pre-canned aggregations, or not run aggregations at all.
Define roles for your users and assign appropriate privileges to ensure that users have access only to the resources that they need. This process determines whether the user behind an incoming request is allowed to run that request.
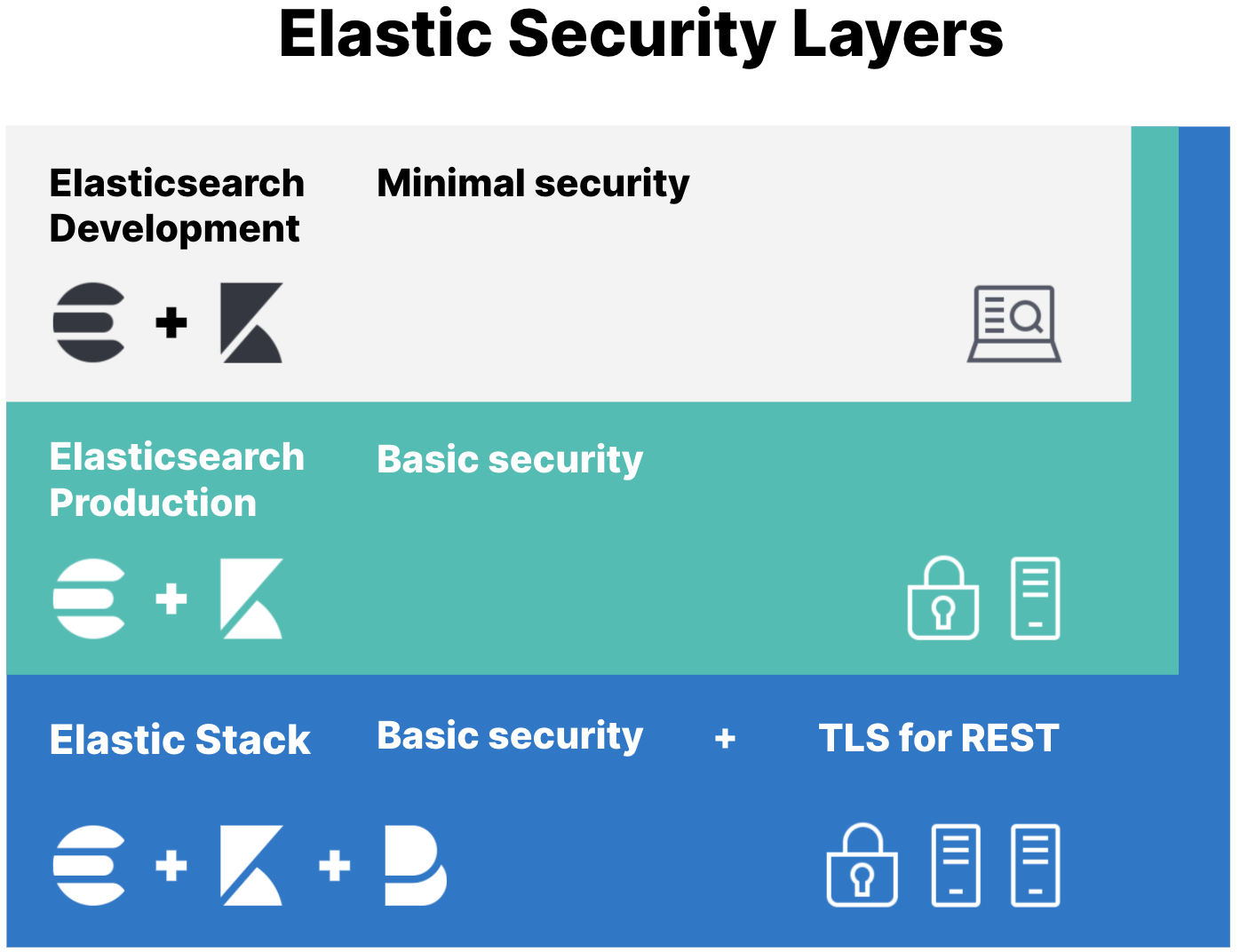
The minimal security scenario is not sufficient for production mode clusters. If your cluster has multiple nodes, you must enable minimal security and then configure Transport Layer Security (TLS) between nodes.
If you’ve been working with Elasticsearch and want to enable security on your existing, unsecured cluster, start here. You’ll set passwords for the built-in users to prevent unauthorized access to your local cluster, and also configure password authentication for Kibana.
This scenario configures TLS for communication between nodes. This security layer requires that nodes verify security certificates, which prevents unauthorized nodes from joining your Elasticsearch cluster.
Your external HTTP traffic between Elasticsearch and Kibana won’t be encrypted, but internode communication will be secured.
This scenario builds on the one for basic security and secures all HTTP traffic with TLS. In addition to configuring TLS on the transport interface of your Elasticsearch cluster, you configure TLS on the HTTP interface for both Elasticsearch and Kibana.
If you need mutual (bidirectional) TLS on the HTTP layer, then you’ll need to configure mutual authenticated encryption.
You then configure Kibana and Beats to communicate with Elasticsearch using TLS so that all communications are encrypted. This level of security is strong, and ensures that any communications in and out of your cluster are secure.
Set up basic security plus HTTPS traffic
When you start Elasticsearch for the first time, the node startup process tries to automatically configure security for you. The process runs some checks to determine:
- If this is the first time that the node is starting
- Whether security is already configured
- If the startup process can modify the node configuration
If any of those checks fail, there’s a good indication that you manually configured security, or don’t want security to be configured automatically. In these cases, the node starts normally using the existing configuration.
If you redirect Elasticsearch output to a file, security autoconfiguration is skipped. Autoconfigured credentials can only be viewed on the terminal the first time you start Elasticsearch. If you need to redirect output to a file, start Elasticsearch without redirection the first time and use redirection on all subsequent starts.
If certain directories already exist, there’s a strong indication that the node was started previously. Similarly, if certain files don’t exist, or we can’t read or write to specific files or directories, then we’re likely not running as the user who installed Elasticsearch or an administrator imposed restrictions. If any of the following environment checks are true, security isn’t configured automatically.
- The Elasticsearch
/datadirectory exists and isn’t empty - The existence of this directory is a strong indicator that the node was started previously, and might already be part of a cluster.
- The
elasticsearch.ymlfile doesn’t exist (or isn’t readable), or theelasticsearch.keystoreisn’t readable - If either of these files aren’t readable, we can’t determine whether Elasticsearch security features are already enabled. This state can also indicate that the node startup process isn’t running as a user with sufficient privileges to modify the node configuration.
- The Elasticsearch configuration directory isn’t writable
- This state likely indicates that an administrator made this directory read-only, or that the user who is starting Elasticsearch is not the user that installed Elasticsearch.
The following settings are incompatible with security auto configuration. If any of these settings exist, the node startup process skips configuring security automatically and the node starts normally.
node.rolesis set to a value where the node can’t be elected asmaster, or if the node can’t hold dataxpack.security.autoconfiguration.enabledis set tofalsexpack.security.enabledhas a value setAny of the
xpack.security.transport.ssl.*orxpack.security.http.ssl.*settings have a value set in theelasticsearch.ymlconfiguration file or in theelasticsearch.keystoreAny of the
discovery.type,discovery.seed_hosts, orcluster.initial_master_nodesdiscovery and cluster formation settings have a value setNoteExceptions are when
discovery.typeis set tosingle-node, or whencluster.initial_master_nodesexists but contains only the name of the current node.