Native user authentication
ECE ECK Elastic Cloud Hosted Self Managed
The easiest way to manage and authenticate users is with the internal native realm. You can use Elasticsearch REST APIs or Kibana to add and remove users, assign user roles, and manage user passwords.
In self-managed Elasticsearch clusters, you can also reset passwords for users in the native realm using the command line.
This topic describes using the native realm at the cluster or deployment level, for the purposes of authenticating with Elasticsearch and Kibana.
You can also manage and authenticate users natively at the following levels:
- For an Elastic Cloud Enterprise installation.
- For an Elastic Cloud organization.
The native realm is available and enabled by default. You can disable it explicitly with the following setting.
xpack.security.authc.realms.native.native1:
enabled: false
You can configure a native realm in the xpack.security.authc.realms.native namespace in elasticsearch.yml. Explicitly configuring a native realm enables you to set the order in which it appears in the realm chain, temporarily disable the realm, and control its cache options.
Add a realm configuration to
elasticsearch.ymlunder thexpack.security.authc.realms.nativenamespace. It is recommended that you explicitly set theorderattribute for the realm.NoteYou can configure only one native realm on Elasticsearch nodes.
See Native realm settings for all of the options you can set for the
nativerealm. For example, the following snippet shows anativerealm configuration that sets theorderto zero so the realm is checked first:xpack.security.authc.realms.native.native1: order: 0NoteTo limit exposure to credential theft and mitigate credential compromise, the native realm stores passwords and caches user credentials according to security best practices. By default, a hashed version of user credentials is stored in memory, using a salted
sha-256hash algorithm and a hashed version of passwords is stored on disk salted and hashed with thebcrypthash algorithm. To use different hash algorithms, see User cache and password hash algorithms.Restart Elasticsearch.
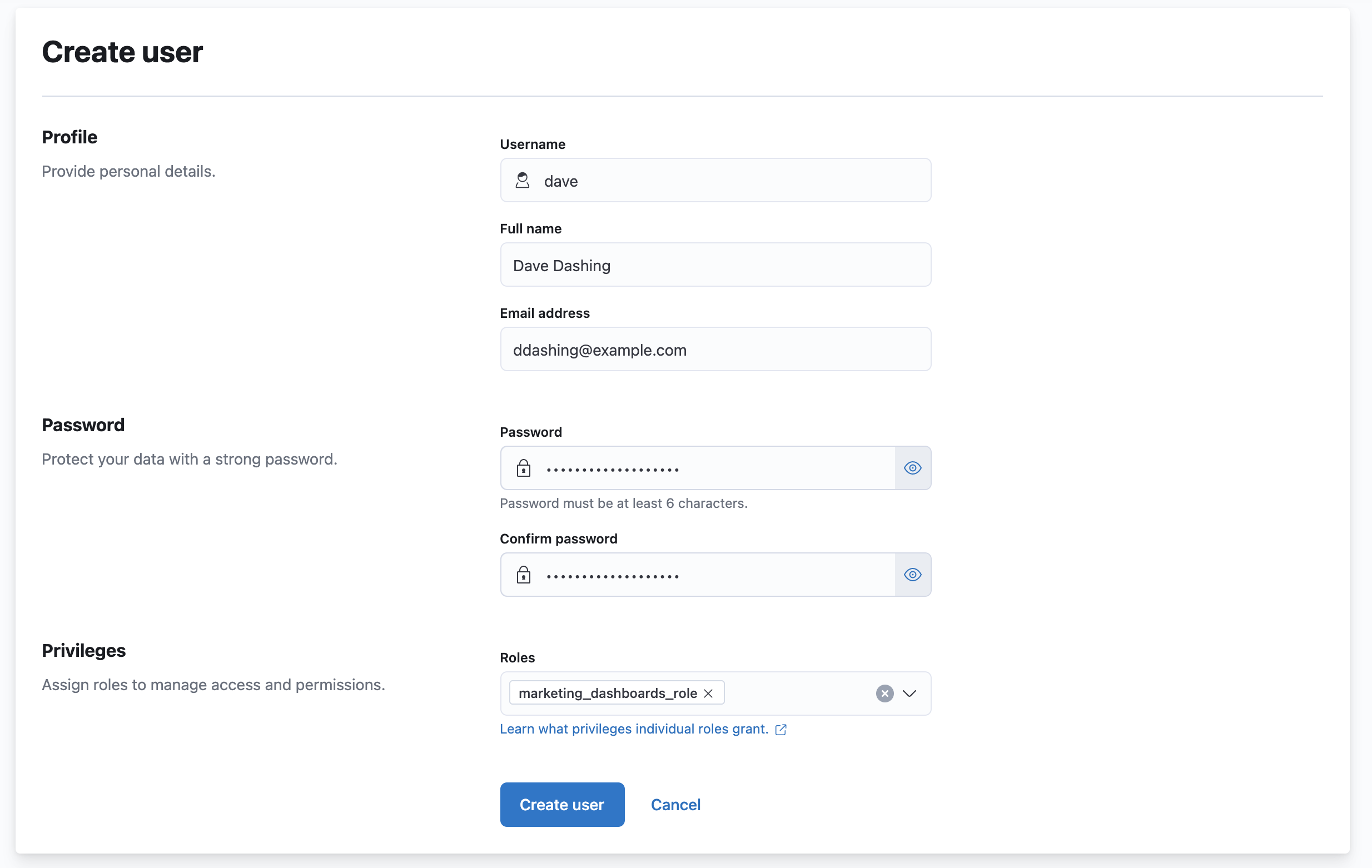
Elastic enables you to easily manage users in Kibana on the Stack Management > Security > Users page. From this page, you can create users, edit users, assign roles to users, and change user passwords. You can also deactivate or delete existing users.
- Navigate to Stack Management, and under Security, select Users.
- Click Create user.
- Give the user a descriptive username, and choose a secure password.
- Optional: assign roles to the user.
- Click Create user.
You can manage users through the Elasticsearch user API.
For example, you can change a user's password:
POST /_security/user/user1/_password {
"password" : "new-test-password"
}
For more information and examples, see Users.
Self Managed
You can also reset passwords for users in the native realm through the command line using the elasticsearch-reset-password tool.
For example, the following command changes the password for a user with the username user1 to an auto-generated value, and prints the new password to the terminal:
bin/elasticsearch-reset-password -u user1
To explicitly set a password for a user, include the -i parameter with the intended password.
bin/elasticsearch-reset-password -u user1 -i <password>